|
Product Overview |
Product Advantage |
|
Technical Advantages
Apply Neusoft’s original ICA (Integrated Check Architecture) of the NetEye technology to collect traffic information from network devices of different layers, such as flow data, SNMP information, raw data package and BGP routing, and organically combine various data sources to detect network abnormity and network attacks in an all-round way;
Excellent protocol analysis capability: Capable of effectively detecting attack, junk mail and worm virus, etc., and completely restoring the contents;
Take corresponding preventive measures for abnormal traffic automatically and protect normal operation of the network;
Address locating and tracking function: Map attacks to physical topography of the network and physically insolate the abnormal traffic in time.
Typical Deployment
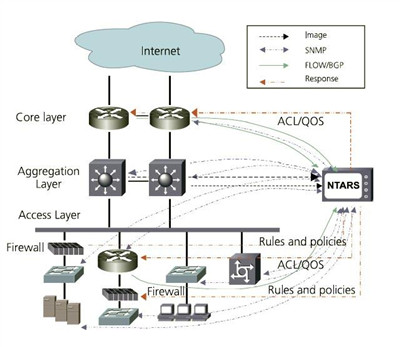
NetEye NTARS is a rack-mount hardware device with more than two 1,000M network ports. It connects to the network by bypass means, plus switch mirror function as optional.
The response system includes anti-junk mail system connected to firewall, IPS, UTM and network devices. Each response system is deployed at the node that needs protection according to its functional features.
|
|
System Features
-
An overall abnormal traffic analyzer and response system integrating multiple inspection methods, including characteristic matching, abnormity recognition, protocol analysis, behavior analysis, and application audit, etc.;
-
Adopt classified inspection technologies for different attacks. Use abnormity detection method to detect and reject abnormal traffic such as service attacks and worm outbreak; Use characteristic matching method to detect attacks with identified characteristics; Use anti-virus engine to detect transmission of vicious files such as virus, worms and Trojans; Use enhanced Bayesian algorithm to detect junk mail to accurately and comprehensively detect various attacking behaviors;
-
Analysis engine adopts a dedicated server design and standard rack-mount installation, featuring convenient deployment with no need of additional software and hardware. Multiple models are available for application in networks ranging from small and medium enterprise networks to large backbone networks;
Bypass means of deployment is adopted for analysis engine, which does not consume network resources or influence key link communication;
-
B/S infrastructure is adopted so that no independent installation of management control client is needed. Browsers can be used to operate on any node in the network;
-
Support secure management mode: Provide HTTPS and SSH management mode to allow administrators to access this system securely at any location with simple and easy-to-use configuration;
-
Support multiple types of data input: Support data collection using SNMP, flow data and BGP protocol as well as direct data traffic extraction via switch mirror;
-
Support various mainstream flow formats and multiple versions, including Cisco Netflow (including v9), Juniper cflowd and sFlow and Huawei Netstream. The system also supports MPLS service by supporting Netflow v9;
-
Long time monitoring capability: Policy-based (a combination of IP, protocol, port and application type, etc) long time monitoring and analysis of traffic meeting filtering conditions; Equipped with large capacity local storage;
In-depth analysis capability: Complete built-in NetEye abnormal behavior characteristic library to quickly detect abnormal behaviors hidden in the traffic via characteristic matching, content recognition, protocol analysis, behavior analysis technology, etc. At the same time, administrators are allowed to customize threshold for determination of abnormity to increase characteristics for inspection of the customer’s actual network environment;
-
Application service quality tracking: Monitor and make statistics of response delay and load distribution of key applications; Capable of effectively recording the availability of customer’s key application services, such as HTTP, SMTP, FTP and DNS, etc.
-
Professional graphic report: Provide professional statistics inquiry and analyzing tools, output professional graphic reports, support automatic report generation by the system and send it to the administrator. The reports can be exported in standard formats such as Excel and XML, etc.
-
Data audit and inquiry function: The system provides flexible and powerful inquiry function as an effective means of audit for customers;
-
Comprehensive alarm response mechanism: Management interface, system log, mail warning, Email warning, and SNMP Trap, etc. Real-time interact with NetEye SOC and promptly defend attacks via security facilities via boot device ACL, black hole router, firewall, IPS, anti-junk mail system, etc.;
-
Multiple built-in user role and permission-based system management: The roles of system administrator, security administrator and audit administrator are divided, and permission of each user can be controlled;
Support self-audit: The system records detailed information of all operations. Only specific audit administrator have to right to perform inquiry and deleting operations;
-
Automatic storage maintenance function: The system provides local storage space for massive data, and can delete expired history data, maintains distribution of storage space, and automatically backup data at designated time;
Provide built-in default policy template and support customization. Built-in database with automatic maintenance and inquire on demand;
-
Support multi-level distributed deployment: With independent central management module or NetEye Secure Operation Console, several NetEye Network Traffic Analyse and Response Systems can be used to receive instructions from central management console and submit monitoring and analysis result so as to meet the deployment need of large backbone networks.
|
|
| |
|
Hotline
400-655-6789 |
|
|
Download

| |


